Wonderful Info About How To Avoid Attacks

Never click on unsafe links:
How to avoid attacks. British firms say they are facing higher shipping costs and delays of up to four weeks due to houthi attacks in the red sea, a business group said. How to prevent cyber attacks effectively? If you click on malicious links, an automatic download.
A cyberattack is an attempt to steal, alter, destroy, disrupt, or disable information resources and systems found in computer networks and systems. 7 types of cyberattacks. Steps such as deep breathing,.
Steal, encrypt or delete sensitive information. As russia’s war in ukraine enters a third year, president vladimir putin ’s forces have shifted to the offensive and captured the eastern city of. A cyber attack is an attempt by cybercriminals to disable computers, steal data, or use a breached computer system to launch additional attacks.
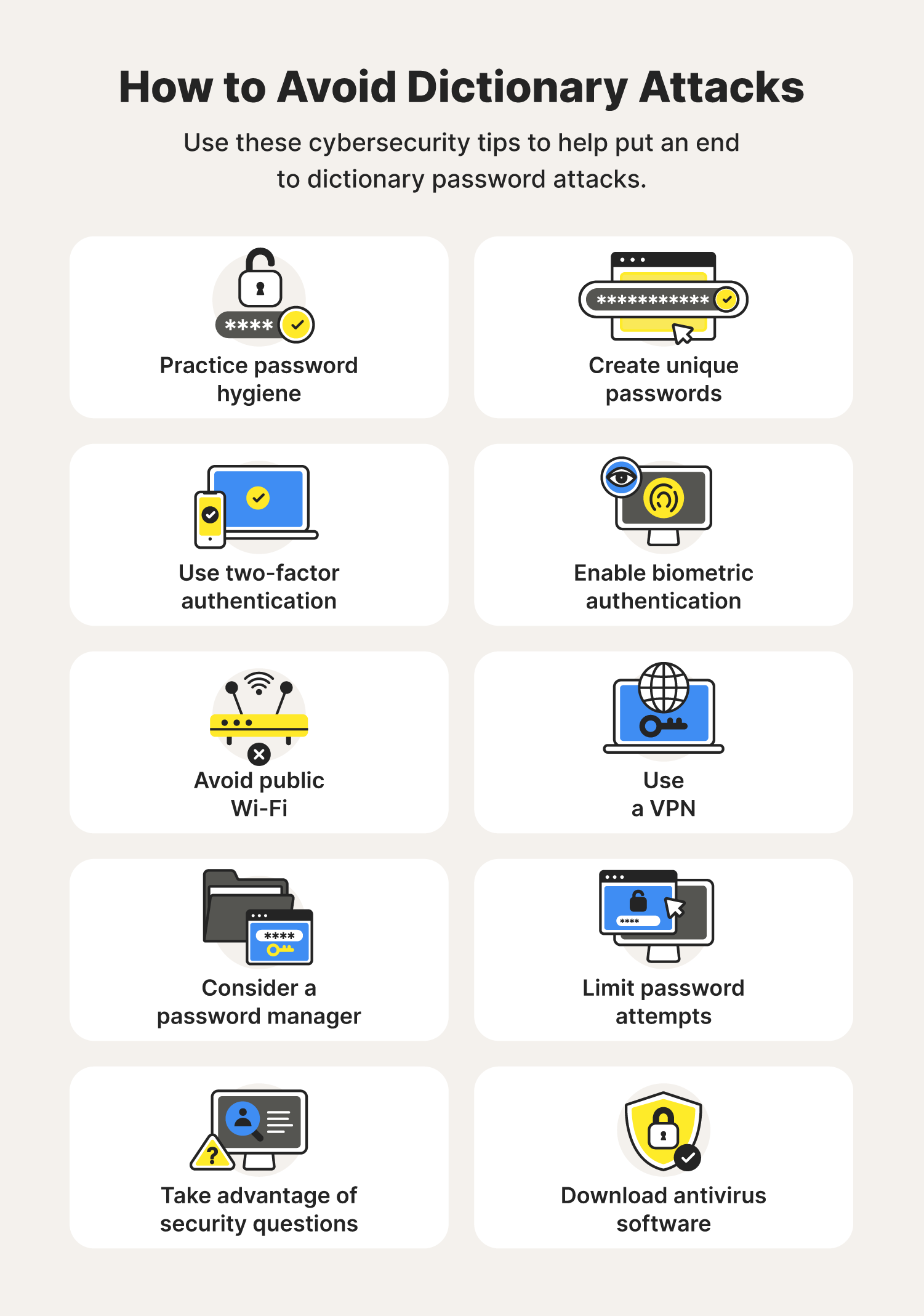
Using caution with email attachments. How to prevent cybersecurity attacks. Address owasp top 10 vulnerabilities.
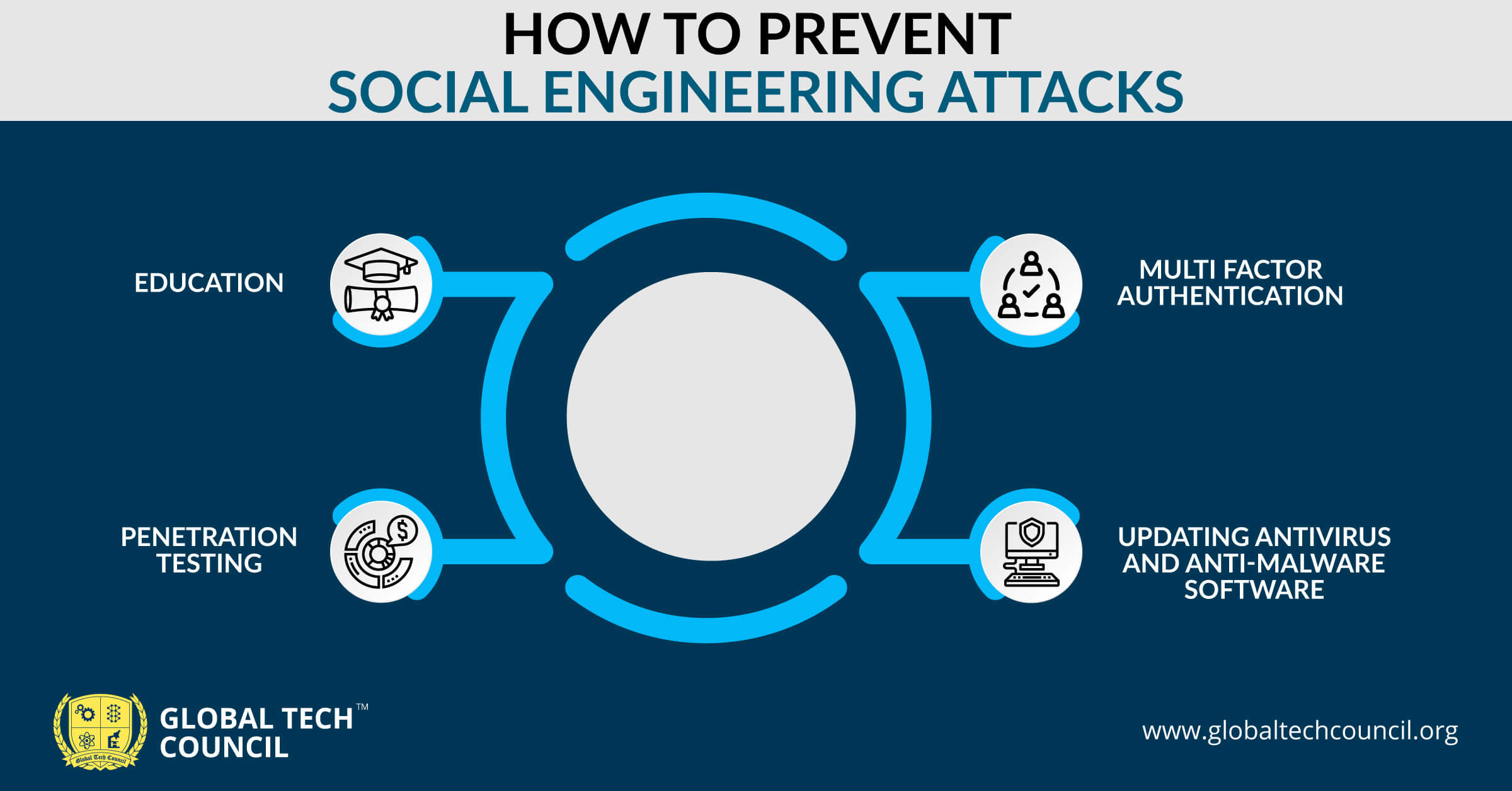
Understanding patches and software updates. Hijack or alter core system functions. Bounty programs and vulnerability disclosure programs (vdp) create a cybersecurity awareness training program.
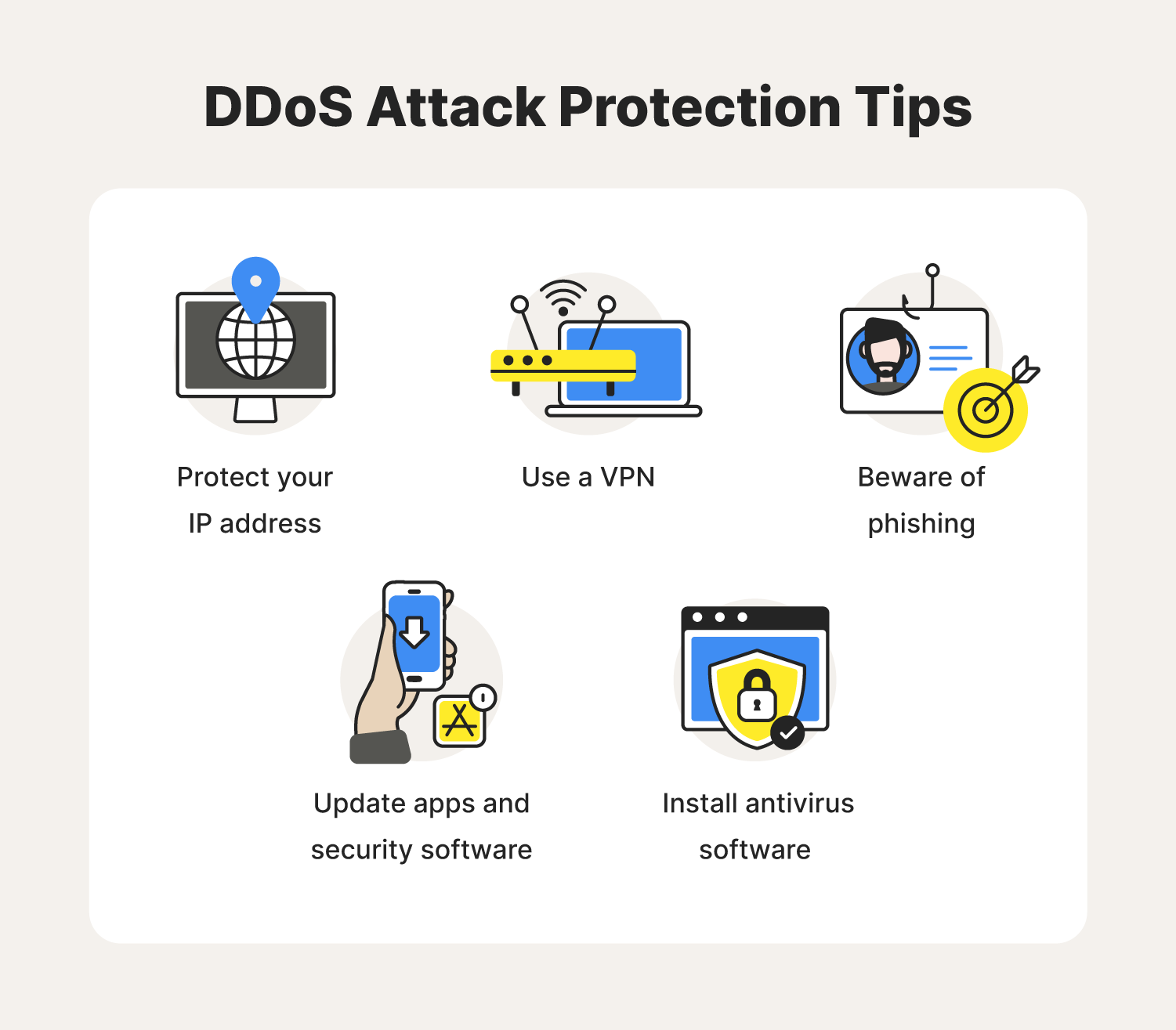
Cyberattacks can fit into two categories: A ddos attack enables a hacker to flood a network or server with bogus traffic. The idea of verifying everything and not trusting anyone has become the most important part of cybersecurity efforts.
Houthi fighters march during a rally of support for palestinians in the gaza strip and against the u.s. Insider threats or outsider threats. Malware is software that infects computer systems to damage, disable or exploit the computer or network to:
How can you stop a panic attack? Research showed that there were 50% more attack attempts on corporate networks in 2021 than in 2020. If you've come across one in your inbox (that hasn’t been auto filtered into spam), use these strategies to avoid becoming a victim of a phishing attack.
Once the malware is on your computer, it can encrypt your data, holding it hostage, only allowing someone with a decryption key to access it. Rising ransomware threat to operational technology assets. Ransomware is a dangerous form of malware that infiltrates computers and mobile devices to kidnap precious files and hold them hostage.
Delete the email without opening it. Limiting attack surface exposure can help minimize the effect of a ddos attack. Based on our experience with ransomware attacks, we’ve found that prioritization should focus on these three steps: