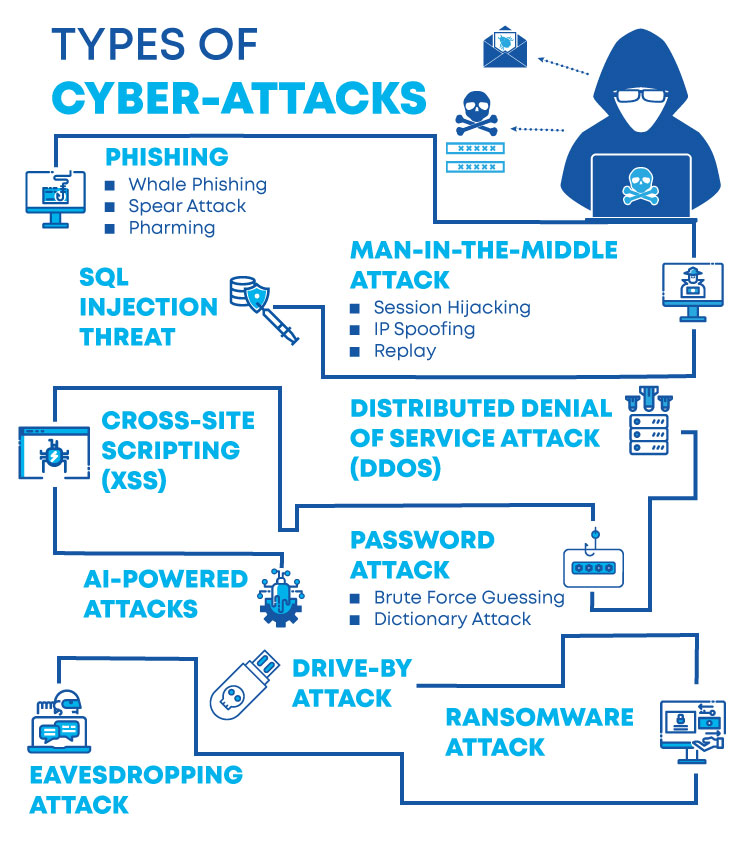
Heartwarming Tips About How To Prevent Computer Attacks

You shouldn’t be using “password” or “12345” for any of.
How to prevent computer attacks. In a standard trojan attack, malware is disguised and packaged into a seemingly. Arguably the most effective thing you can do to protect your online accounts is turning. Apple says it's going to upgrade the cryptographic protocol used by imessage to hopefully prevent the decryption of conversations by quantum computers, should those machines ever exist in a meaningful way.
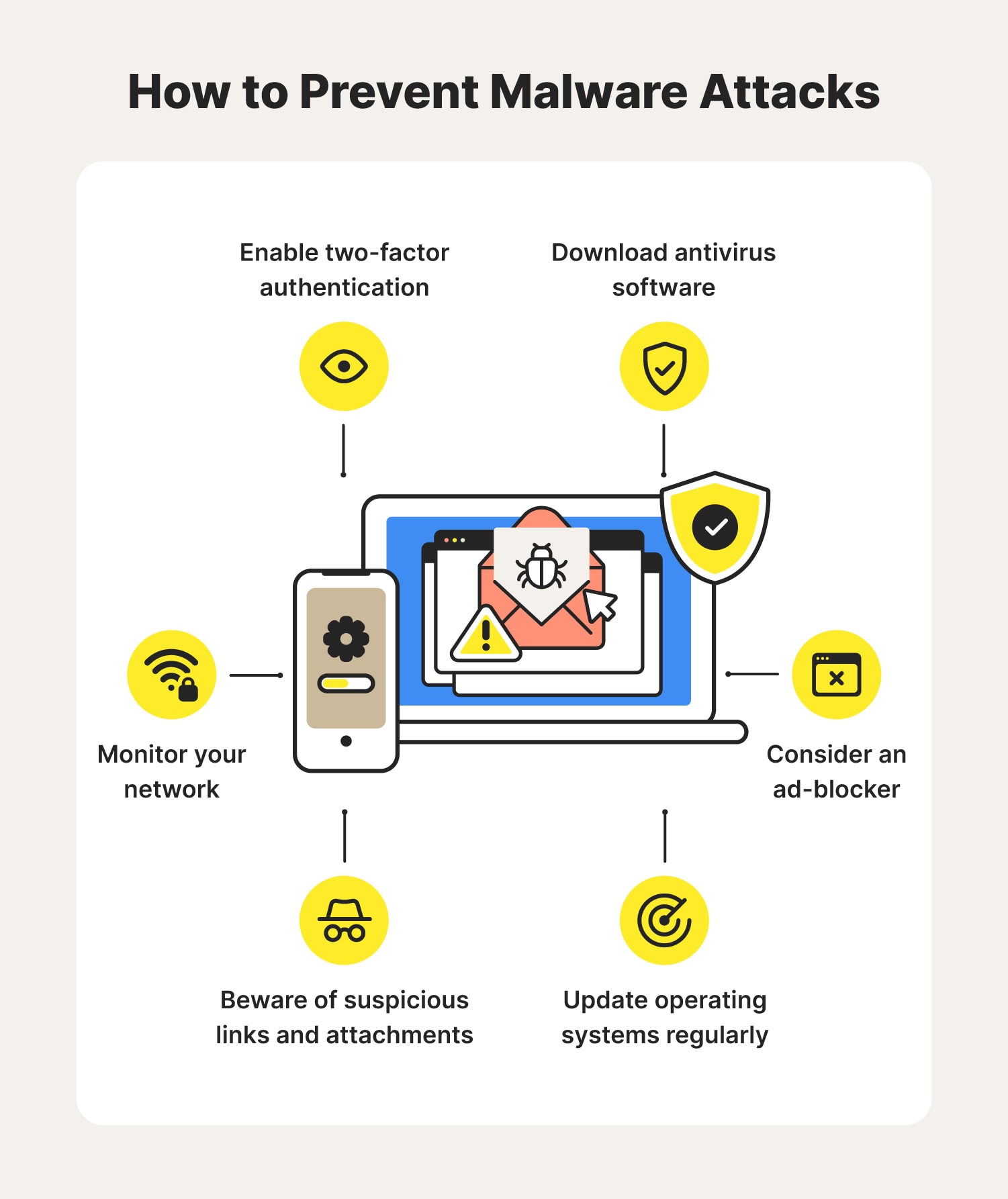
A cyber attack is an attempt by cybercriminals to disable computers, steal data, or use a breached computer system to launch additional attacks. Companies often collect and store personally identifiable information, which can be obtained by. Avoiding malware is possible by following the best practices to prevent it.
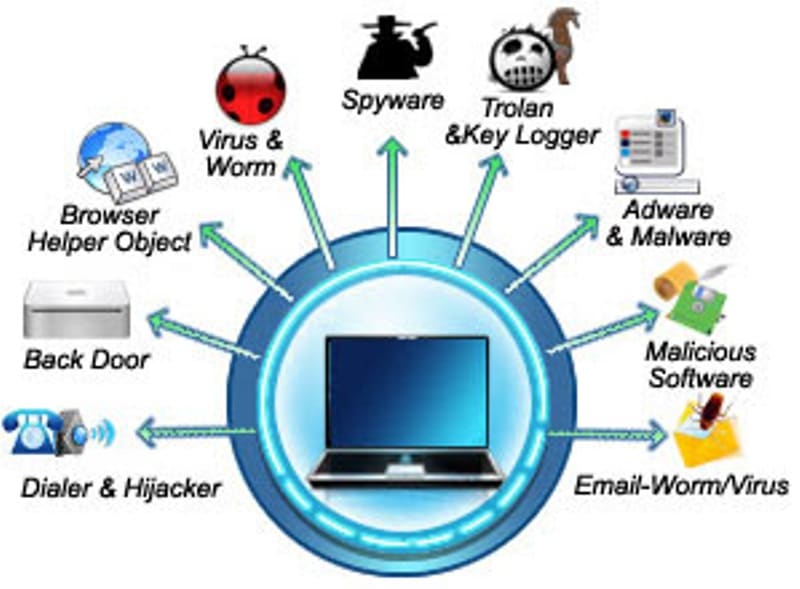
Disguised as a harmless file or application, a rat opens a backdoor to your device via a network, putting your data, security, and identity at risk. Since hackers and cybercriminals are always looking for new ways to exploit network vulnerabilities, business owners must take steps to protect their data and infrastructure. Cyber attacks can take a variety of forms from compromising personal information to capturing control of computers and demanding a ransom—usually paid in the form of cryptocurrency—to release that control.
One of the best ways to protect your computer and data from malware attacks is to make regular backups. A remote access trojan (rat) is a type of trojan cyberattack that gives a hacker remote access to your device. Discover how to prevent malware from infecting your devices.
Here are some general rules to follow to stay safe in 2023. Therefore, it is often listed among the best practices to prevent ransomware. One to keep offline and another to keep in.
Check links before clicking them check email addresses from the received email (have a look here on how to check it) Wed 21 feb 2024 // 21:09 utc. A cybersecurity attack may use one or several attack vectors to target individuals or organizations, and achieve objectives ranging from financial gain to sabotage and terrorism.
As new technology emerges, cybersecurity protocols also evolve. It should spell out the potential consequences of misuse. Malware designed to give a remote hacker control over your device.
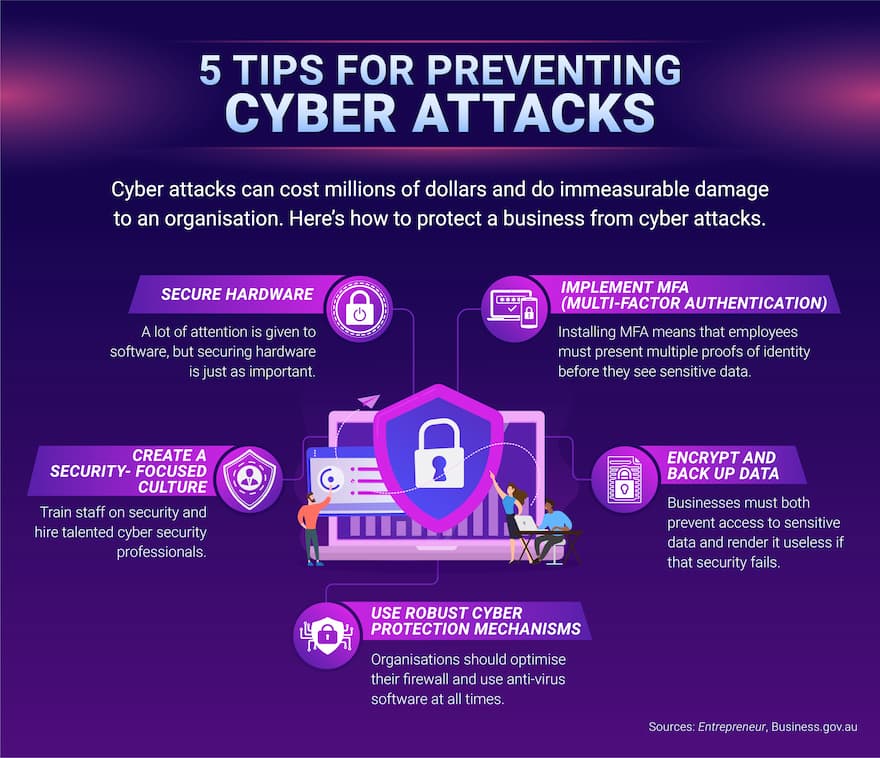
Cyber attacks have become more sophisticated in recent years and, as a result, cyber attack prevention is essential for every individual and organization. Use antivirus software to protect your computer against malware. The main point is to turn your information security radar inward.
Go into the security settings of your computer and look for firewall settings. Compensating controls are security measures you can use to cover for the lack of protection, like putting additional firewall rules or strengthening intrusion detection rules. They work by controlling the network traffic moving through your system.
The reason these attacks spread so quickly is that they are often hard to spot. For all businesses, making sure that staff are aware of the importance of cyber. You should always create at least two backups: